There are currently many ways to attack vulnerability of our computer systems and we must find means that allow us to be safe from attacks of any kind. Hackers don't stop in their quest to find ways to break into our systems and create new ways to do so. For this reason, we will teach you how to enable and configure Exploit protection in Windows 10.
How to enable and configure exploit protection in Windows 10" src="/images/posts/b12e61e20fb5718f24e276950927261e-0.jpg">
Apparently in this new version of Windows, security has become its main task and Windows Defender is up to you with the best antivirus of the world. But another new feature of Windows 10 is the inclusion of Creator Update in its new security center. Which allows users of this operating system to feel a little calmer.
We have already talked in many articles about the safety devices that Windows uses to protect against unwanted software and possible violations of our privacy. Or you can view and manually delete quarantined files in Windows Defender, quickly and easily.
How to enable and configure exploit protection in Windows 10
This new way to protect your system from Exploit attacks is enabled by default in Windows 10 Fall Creator Update. We can disable or enable this feature at any time, as appropriate. And make configurations in its different modules to change the protection levels.
We can also choose those programs that we want to protect from possible attacks, as these may be more vulnerable.
This way we can feel more confident in the protection this tool can provide to our team. And then we'll explain what you need to do for activate and configure it.
Steps to enable and configure exploit protection in Windows 10
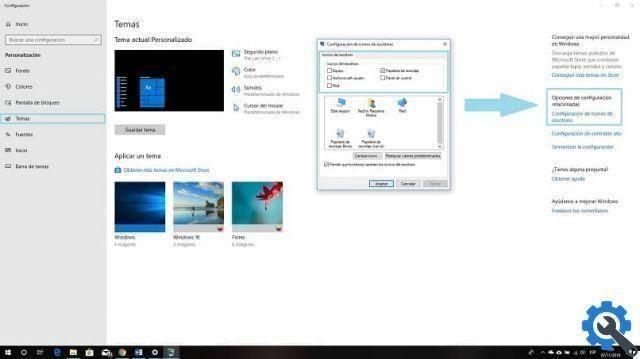
The first step in setting up security against Exploit attacks is to enter Windows Defender and we will do it via the security center. Once there, we need to go to the Application and Browser Control section. Being in this window, we will look for the option Protection against vulnerability, we will do it if we move towards the end of the window.
Once this option is chosen, we will go to the Settings section and here we will select the Anti-exploit settings option of Windows Defender.
Entering this new window, we will observe the different active options that can be configured. If for any reason you want to opt out of any of them, you can do so, although we don't recommend it.
Among the different protections that this tool can provide us against Exploit attacks we can name you. Data Execution Prevention, Control Flow Protection, Random Memory Allocations, Force Random Image Selection. Validate heap integrity, validate exception strings.
Now, if what we want is to protect an application or program from a possible Exploit attack, we should just exit this section and go to Settings of the program. By selecting this option, we will enter its window and we will be able to see that Windows Defender already keeps all applications and programs under its protection.
But in the same way we can remove the protection in any application or adjust its level, as well as the type of shield that we want to apply to that program.
Remember that there are different techniques for attacking Exploit. And each shield specializes in one in particular, which prevents them from exploiting any vulnerabilities.
How to enable and configure exploit protection in Windows 10" src="/images/posts/b12e61e20fb5718f24e276950927261e-1.jpg">
This is how we conclude this interesting article, which could shed light on such an important aspect in the security of our IT systems, let's try to explain such complex issues in a simple way. And teach you how enable and configure Exploit protection in Windows 10.